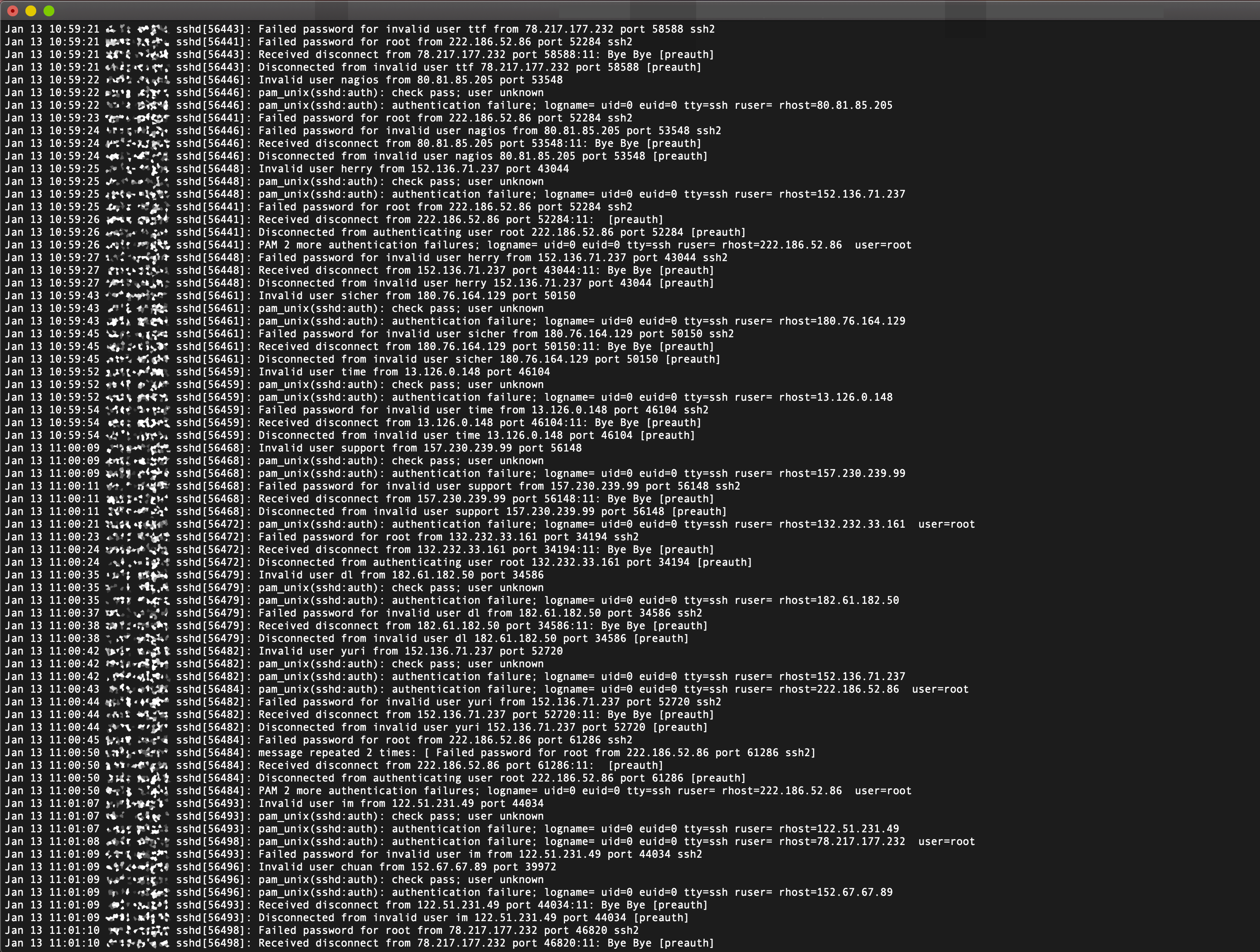
Reduce SSH brute force attacks by changing your default SSH server (sshd) port from port 22 to a
different one. Below is a sshd log example of a brute force attacks.
Changing the port
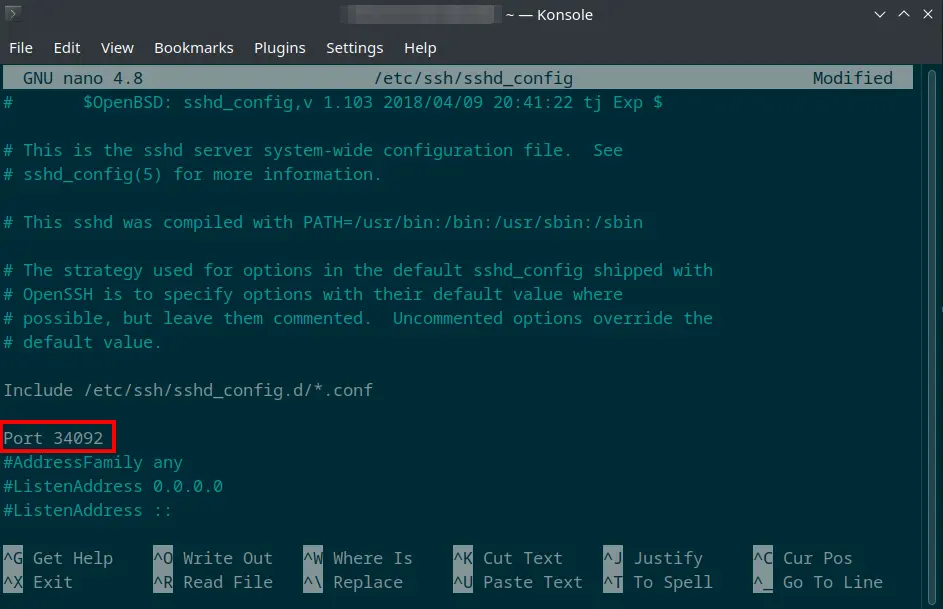
You can change the default port by editing the sshd configuration file.
sudo nano /etc/ssh/sshd_config
Find the line that say #Port. Remove the # symbol and set the port number you prefer. Refer to the image below as reference.
Logging In
After changing the SSH port, you can now login using the following commands:
ssh
ssh -p 34092 [email protected]
scp
Transfer files using scp with capital -P as parameter
scp -P 34092 file.txt [email protected]:file.txt
rsync
Push
rsync -azvP -e 'ssh -p 34092' SOURCE USER@HOST:DEST
Pull
rsync -azvP -e 'ssh -p 34092' USER@HOST:SOURCE DEST
Conclusion
This is just one way to reduce brute force attacks. You can further harden your server by using a firewall that only allows connections from specific IP or IP ranges. You can also use Fail2Ban, a software that automatically blocks users who already reached the invalid attempt count.